Multiparty Computation: How it Allows for Secure Collaboration
Discover how Multiparty Computation (MPC) ensures privacy in sensitive computations. Learn its purpose, properties, and step-by-step examples featuring real-life scenarios like salary averaging.
Introduction
Cryptography serves to keep statements between parties safe and secure. It allows the sending party to send messages only the receiving party will decipher, preventing unauthorized persons from decrypting the message even if it was intercepted en route.
Back in the 1980s, Andrew Yao introduced MPC. It allows several folks to compute things together over their inputs while keeping those inputs private. This is different from traditional cryptographic goals because instead of focusing just on secure communication, MPC makes sure computations stay secure without requiring trust among participants.
Some of the main properties of MPCs include:
-
Confidentiality - where each participant’s input stays private.
-
Correctness - ensures that the results are just as accurate as if done by a trusted third party.
-
Independence - allows for each party to not reveal their inputs to anyone else.
An MPC is like a bridge, linking privacy with usability. It helps out with use cases like secure voting, auctions & collaboration in fields such as healthcare and finance.
Types of Party Computations
Secure computations can be set up differently based on the number of participants and the desired purpose:
- Two-Party Computation
Suppose Anne and Peter want to compare who among them earns a higher salary without disclosing their salaries. A two-party protocol like Yao’s Garbled Circuits helps them securely compute the result.
- Multiparty Computation
In this type of computation, we have more than two parties that split inputs and shares them among the participants. The computation jigsaw is achieved without having the participants sharing their private data.
Let’s say three friends: Anne, Peter & Keith each have different salaries ($100k, $80k & $120k), and would want to know the average salary in the group. However, each of them would want to keep individual salaries a secret.
To compute their average salary they use Multiparty Computation as follows:
- Step 1: Secret Sharing
-
Anne will divide her $100k salary into three shares: $40k, $30k & $30k.
-
Peter and Keith repeat the same process with their own salary amounts.
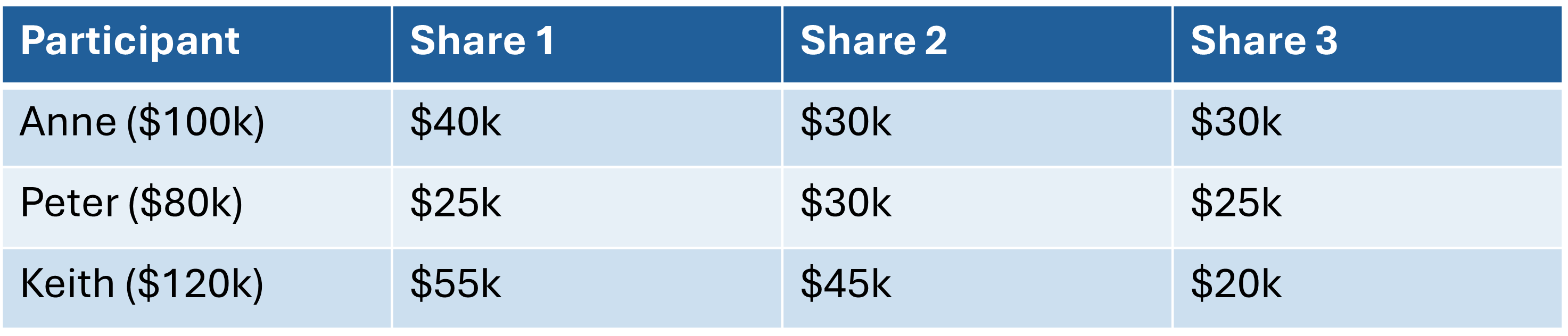
- Step 2: Share Distribution
- Each participant will keep a share of the amount and distribute the rest to each party.
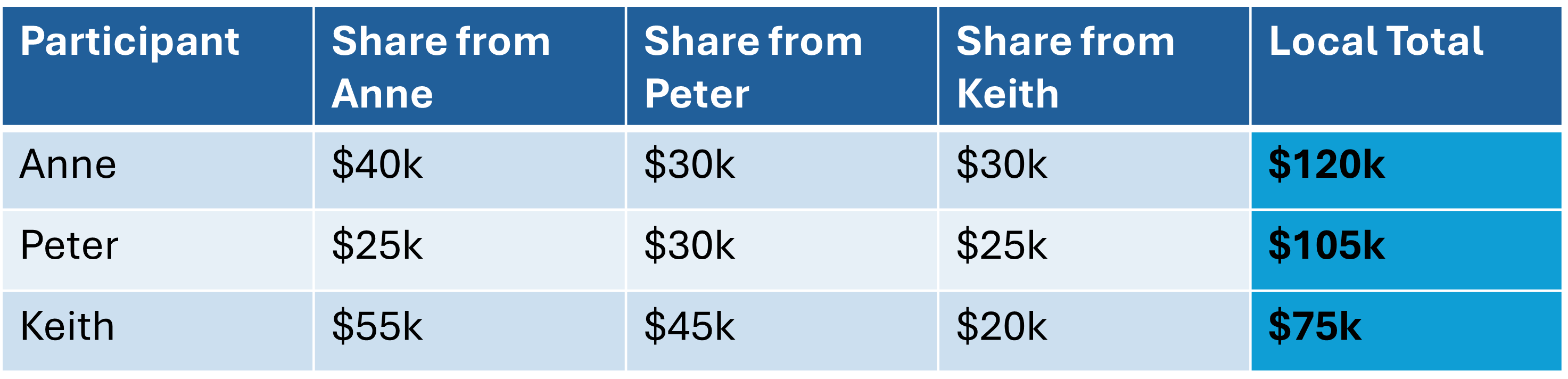
- Step 3: Local Computation
- Each participant computes the sum of their received shares.
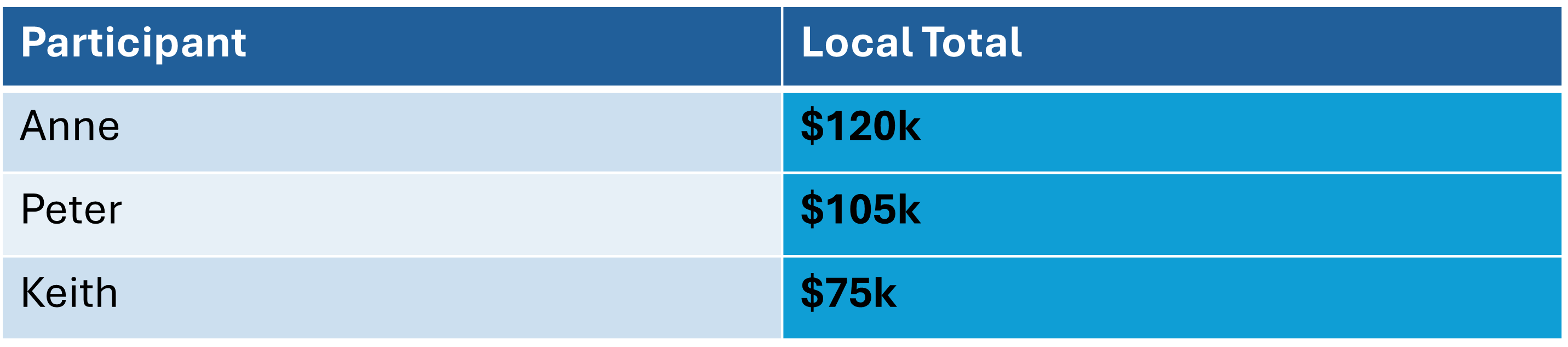
- Step 4: Result Reconstruction
-
Totaling up all local computations and dividing by the number of participants results in an average salary of $100K.
Total Sum = $120k + $105k + $75k = $300k
Average Salary = Total Sum/No. of Participants = $300k/3 = $100k
Why MPC Is Effective Compared to Other Cryptographic Tasks
Unlike some encryption paths like homomorphic encryption, MPC doesn’t need a centralized authority or trusted third party. Due to its distributed nature, it ensures that:
-
Data privacy is preserved throughout the entire duration of the computation.
-
It is resilient against single-point-of-failure attacks.
-
Multiple parties can collaborate on sensitive tasks.
Conclusion
Multiparty Computation flips traditional cryptography on its head by enabling safeguarding works that balance secure outcomes with personal secrets kept intact. With its theoretical and practical grounding wrapped in one tidy bow, MPC empowers qualified cooperative work without elbowing privacy out of the way.
In the next article, we will dive deeper into protocols and practical implementations demonstrating how Multiparty Computation works in real-world applications.